Secure Software Development
- Setting secure SDLC Practices in development
- Source Code Security
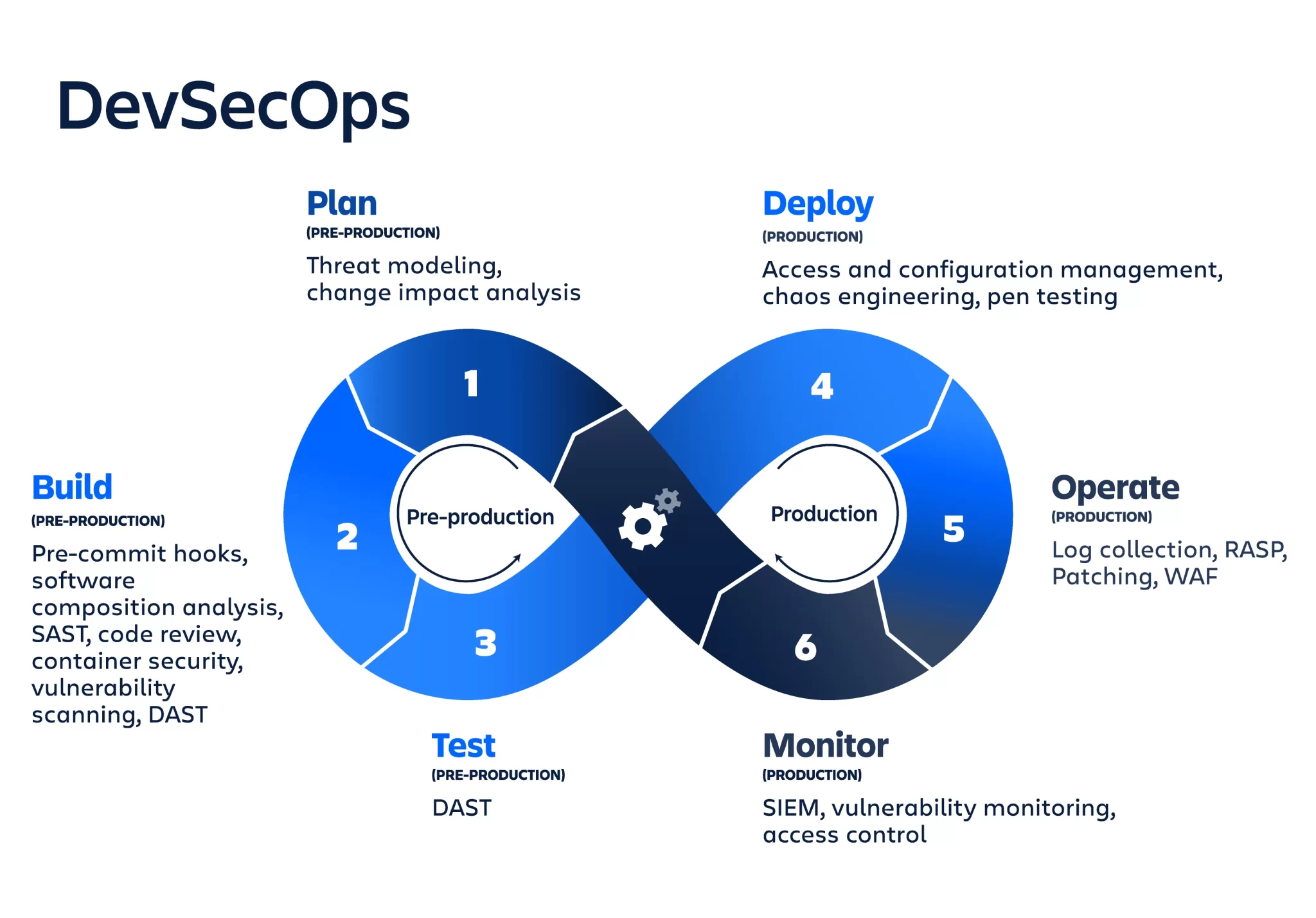
Implementing secure SDLC practices in development ensures that security is integrated into every phase of the software development process, reducing vulnerabilities and enhancing overall software quality. Here are key practices to consider:
Security Requirements Analysis: Define security requirements alongside functional requirements during the planning phase to ensure security is built into the project from the start.
Threat Modeling: Identify potential threats and vulnerabilities early in the design phase to mitigate risks before they become significant issues.
Secure Coding Standards: Enforce secure coding practices, such as input validation and proper error handling, to prevent common vulnerabilities like SQL injection, cross-site scripting (XSS), etc.
Code Review and Static Analysis: Regularly conduct code reviews and use static analysis tools to detect and fix security flaws in the codebase before deployment.
Automated Security Testing: Integrate automated security testing tools, such as SAST (Static Application Security Testing) and DAST (Dynamic Application Security Testing), into the CI/CD pipeline to identify security issues continuously.
Patch Management: Keep libraries, frameworks, and dependencies up to date to protect against known vulnerabilities by implementing a proactive patch management process.
Security Training and Awareness: Provide ongoing security training and awareness programs for developers to keep them informed about the latest security threats and best practices.
Source code security involves safeguarding the integrity, confidentiality, and availability of the source code throughout the software development process. Protecting source code is crucial as it contains the business logic, algorithms, and sensitive data that can be exploited if compromised. We are considering some best practices to enhance source code security:
Access Control: Implement strict access controls using the principle of least privilege, ensuring that only authorized personnel can access or modify the source code.
Version Control Systems: Use secure version control systems (like Git) with proper authentication and encryption to track changes and prevent unauthorized access.
Code Review and Audits: Conduct regular code reviews and audits to detect vulnerabilities and enforce coding standards. Peer reviews also help in identifying security weaknesses that automated tools might miss.
Static Code Analysis: Use static code analysis tools to automatically scan the source code for common security issues, such as buffer overflows, unvalidated inputs, and improper error handling.
Encryption: Encrypt sensitive code repositories and data in transit to prevent unauthorized access and eavesdropping.
Dependency Management: Regularly update and monitor dependencies to avoid vulnerabilities in third-party libraries that could compromise the security of the source code.
Secure Coding Practices: Follow secure coding guidelines, such as input validation, output encoding, and proper error handling, to minimize the risk of introducing security flaws.
Continuous Integration/Continuous Deployment (CI/CD) Security: Secure CI/CD pipelines by integrating security testing tools, enforcing code signing, and monitoring for any suspicious activities.